From Thanos to Prometheus: When Ransomware Encryption Goes Wrong
This post was researched by X-Force's Aaron Gdanski who broke Prometheus's encryption. He is set to present this research at the 2022 RSA Conference in San Francisco.
---
IBM
Security X-Force researchers have recently reverse-engineered Prometheus
ransomware samples as part of ongoing incident response operations. X-Force has
found that samples that infected organizational networks featured flawed
encryption. This allowed our team to develop a fast-acting decryptor and help
customers recover from the attack without a decryption key.
While
rare, ransomware developers can make mistakes in the ways they implement
encryption, causing unintended flaws. This is not the first time X-Force sees
faulty encryption mechanisms save the day for victimized organizations.
Mistakes can easily occur when malware developers use patchwork code and dabble
in cryptography without appropriate expertise.
Most
organized cybercrime groups do use properly configured encryption, which is
almost always impossible to break. That said, the option to examine
possibilities can make a difference for victimized organizations and change the
course of negotiation and recovery.
Thanos Breeds Hakbit, Prometheus, Haron and More Ransomware Trouble
In
early 2020, a new ransomware family dubbed “Thanos” was discovered on sale in
underground forums mostly frequented by cybercriminals. At the time, Thanos was
advertised as a “Ransomware Affiliate Program,” available for anyone to buy.
The malware saw regular updates and new features added over time. A closer look
at its code revealed that it was also used at the baseline in ransomware
samples that were tracked as “Hakbit” and used in additional attacks that
targeted organizations in Austria, Switzerland and Germany.
Thanos’
developer equipped it with a bootlocker in mid-2020 and was also using a
somewhat novel technique of encrypting files known as “RIPlace,” in which they
weaponized research into ransomware evasion techniques based on file
characteristics.
In
September 2020, Thanos was detected in attacks on government organizations in
MEA. It presented the victims with a black screen that demanded money to unlock
files, and while it had a supposed capability to run a destructive attack, that
function did not work and left MBR intact.
By
June 2021, more of Thanos made headlines, only this time as the base code for
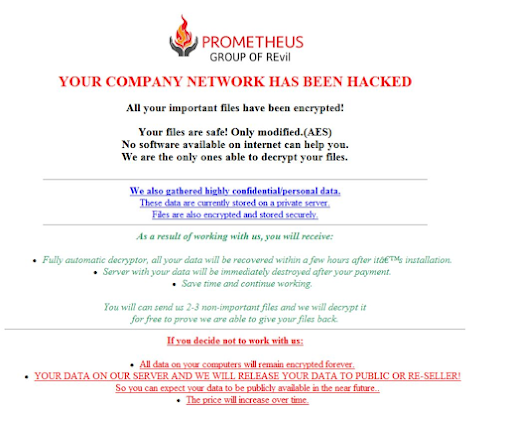
another ransomware, Prometheus. The latter was used in double-extortion attacks
that encrypted files but also stole data and threatened to release it unless a
hefty ransom was paid. Prometheus’ operators claimed to be part of the REvil
group, they even placed a logo of sorts on their demands for ransom but
provided no proof to that effect and may have wanted to use that as a pressure
tactic.
Continue reading the technical details here.

Comments
Post a Comment