I’m Yelling Tinba! Trojan Sets Sights on Singapore Banks for Holiday Season
IBM
X-Force malware researchers have uncovered an aggressive malware campaign
targeting banks in Asia. The campaign, which uses the Tinba v3 banking Trojan
to infect potential victims, has its sights set on business and corporate
accounts held with nine major bank brands in Singapore.
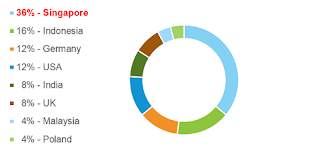
While
other countries are also targeted, the amount of Singaporean bank brands on the
malware gang’s list top the chart. The country accounts for more than one-third
of all targeted brands.
New Tinba v3 Campaign Targets Accounts in Singapore
The
second half of 2015 has revealed a strong attack trend on high-value accounts
of all types as cybercrime gangs attempt to diversify the sources they target
and increase the amount of money they steal in each illicit transaction. This
trend seems to indicate that more gangs than ever have set up the necessary
infrastructure to launch such attacks and successfully make large transfers to
offshore accounts.
Tinba v3
is known to be operated by a gang that uses three principal configurations to
attack different regions in the world. The configuration currently targeting
Singaporean banks is Asia-specific and has been further adapted to harvest user
credentials for business and corporate accounts. In that same configurations
file, the list of targeted URLs includes online trading sites, personal account
credentials and credentials to access the accounts of users who browse to
Singapore’s principal credit bureau.
Read more
of this post here.

Comments
Post a Comment