Overnight Sensation — CoreBot Returns as a Full-Fledged Financial Malware
Just
last month, Security Intelligence warned about a new and modular
Trojan called CoreBot, indicating its internal structure suggested a new
threat about to evolve.
CoreBot’s
developers did not wait long. Within a matter of days, new samples of CoreBot,
discovered and analyzed by IBM X-Force researchers, revealed that the malware
has become a full-fledged banking Trojan — almost overnight. This seemingly
quick evolution is most likely due to a longer development and testing phase
that just recently ended.
What has
been added to CoreBot to become a banking Trojan? In short:
· Browser hooking for Internet Explorer, Firefox and Google
Chrome;
· Generic real-time form-grabbing;
· A virtual network computing (VNC) module for remote
control;
· Man-in-the-middle (MitM) capabilities for session
takeover;
· Preconfigured URL triggers to target banks;
· A custom web-injection mechanism;
· On-the-fly webinjections from a remote server.
CoreBot’s Targets
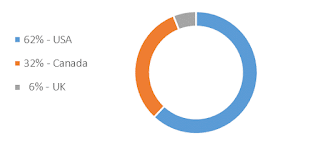
CoreBot
now comes with a list of 55 URL triggers that launch it into action. All
triggers are online banking sites in the U.S., Canada and the U.K. The triggers
include the corporate banking, business banking and private banking pages of 33
target financial institutions.
CoreBot’s
configuration file appears to be using a trigger format that is very similar to
Dyre’s, where not all URLs are very precise. Rather, the triggers are written
in regular expressions (RegEx) format, which helps the Trojan fixate on URL
patterns and thus target a wider array of financial institutions that use the
same electronic banking platforms.
CoreBot’s New Financial M.O.
Read
more about this malware here

Comments
Post a Comment